Enable HTTPS on your Website for Free Cont...
Https , Ssl , Certbot , Letsencrypt / May 31, 2019
Now let’s try to automate the certificate generation. For this I am going to refer to a post published on pbxhacks.com. Please do exercise caution when you try the scripts below as they will change all the TXT records in your domain.
--manual-auth-hook and --manual-cleanup-hook options in certbot can be used to add the TXT record and delete it once the DNS Challenge is completed.
auth.sh
This script will add the TXT record and wait until that record is available to be verified.
# auth.sh
#!/bin/bash
# http://pbxhacks.com/automating-lets-encrypt-ssl-certs-via-godaddy-dns-challenge/
# GoDaddy Credentials
GODADDY_API_KEY="<YOUR API KEY>"
GODADDY_API_SECRET="<YOUR API SECRET>"
GODADDY_URL="https://api.godaddy.com"
# DNS Settings
DNS_REC_TYPE=TXT
DNS_REC_NAME_BASE="_acme-challenge"
DNS_REC_DATA="$CERTBOT_VALIDATION"
DNS_REC_TTL="600"
DNS_REC_NAME=${DNS_REC_NAME_BASE}.${CERTBOT_DOMAIN}
GODADDY_DNS_REC_NAME="${DNS_REC_NAME%.*}"
GODADDY_DNS_REC_NAME="${GODADDY_DNS_REC_NAME%.*}"
echo "[[ INFO ]] Adding TXT Record"
if $(curl -X PUT "${GODADDY_URL}/v1/domains/${CERTBOT_DOMAIN}/records/${DNS_REC_TYPE}" -H "accept: application/json" -H "Content-Type: application/json" -H "Authorization: sso-key ${GODADDY_API_KEY}:${GODADDY_API_SECRET}" -d "[{ \"data\": \"${DNS_REC_DATA}\", \"name\": \"${GODADDY_DNS_REC_NAME}\", \"ttl\": ${DNS_REC_TTL} }]" --silent); then
echo "[[ INFO ]] Successfully added TXT Record"
else
echo "[[ ERROR ]] Error Adding TXT Record"
exit 1
fi
sleep 20;
until [[ $(dig -t txt ${DNS_REC_NAME} +short) ]]; do
echo "..."
sleep 5
done
sleep 10;
echo "[[ INFO ]] Success Adding TXT Record"cleanup.sh
Changes the TXT record name since GoDaddy does not have a delete API.
# cleanup.sh
#!/bin/bash
# http://pbxhacks.com/automating-lets-encrypt-ssl-certs-via-godaddy-dns-challenge/
# GoDaddy Credentials
GODADDY_API_KEY="<YOUR API KEY>"
GODADDY_API_SECRET="<YOUR API SECRET>"
GODADDY_URL="https://api.godaddy.com"
# DNS Settings
DNS_REC_TYPE=TXT
DNS_REC_NAME_BASE="old_acme-challenge"
DNS_REC_DATA="$CERTBOT_VALIDATION"
DNS_REC_TTL="600"
DNS_REC_NAME=${DNS_REC_NAME_BASE}.${CERTBOT_DOMAIN}
GODADDY_DNS_REC_NAME="${DNS_REC_NAME%.*}"
GODADDY_DNS_REC_NAME="${GODADDY_DNS_REC_NAME%.*}"
echo "[[ INFO ]] Changing TXT Record"
if $(curl -X PUT "${GODADDY_URL}/v1/domains/${CERTBOT_DOMAIN}/records/${DNS_REC_TYPE}" -H "accept: application/json" -H "Content-Type: application/json" -H "Authorization: sso-key ${GODADDY_API_KEY}:${GODADDY_API_SECRET}" -d "[{ \"data\": \"${DNS_REC_DATA}\", \"name\": \"${GODADDY_DNS_REC_NAME}\", \"ttl\": ${DNS_REC_TTL} }]" --silent); then
echo "[[ INFO ]] Successfully Changed TXT Record"
else
echo "[[ ERROR ]] Error Changing TXT Record"
exit 1
fi
echo "[[ INFO ]] Success Cleaning Up"run.sh
Runs Certbot.
#!/bin/bash
DOMAIN=${1:-localhost.kubefire.com}
sudo certbot certonly --manual --preferred-challenges dns --manual-auth-hook ./auth.sh --manual-cleanup-hook ./cleanup.sh --domains $DOMAINObtaining the Certificates
Execute run.sh with the domain to generate the certs. For testing the scripts pass --staging flag to certbot command to not get blacklisted.
./run.sh localpqr.kubefire.com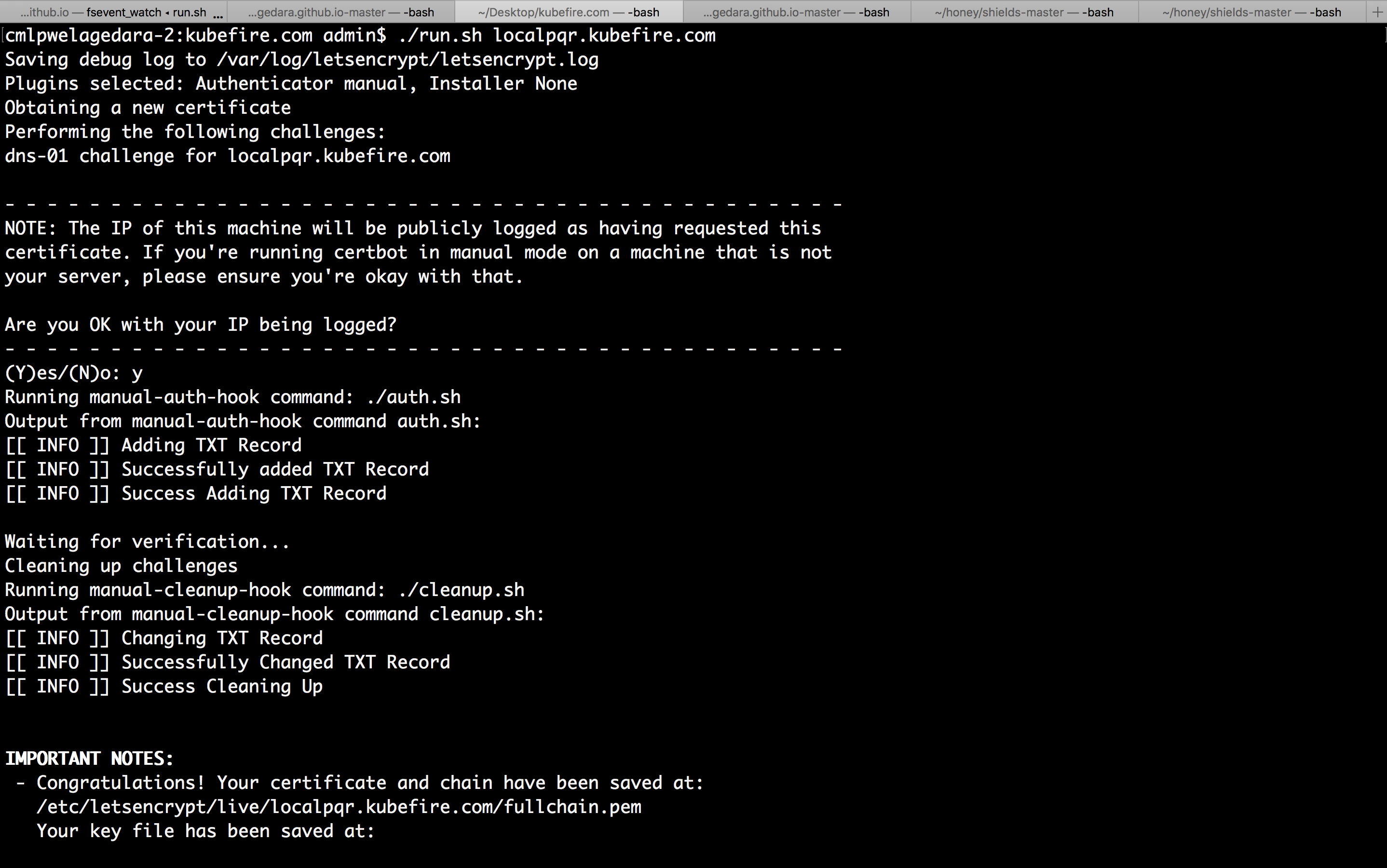
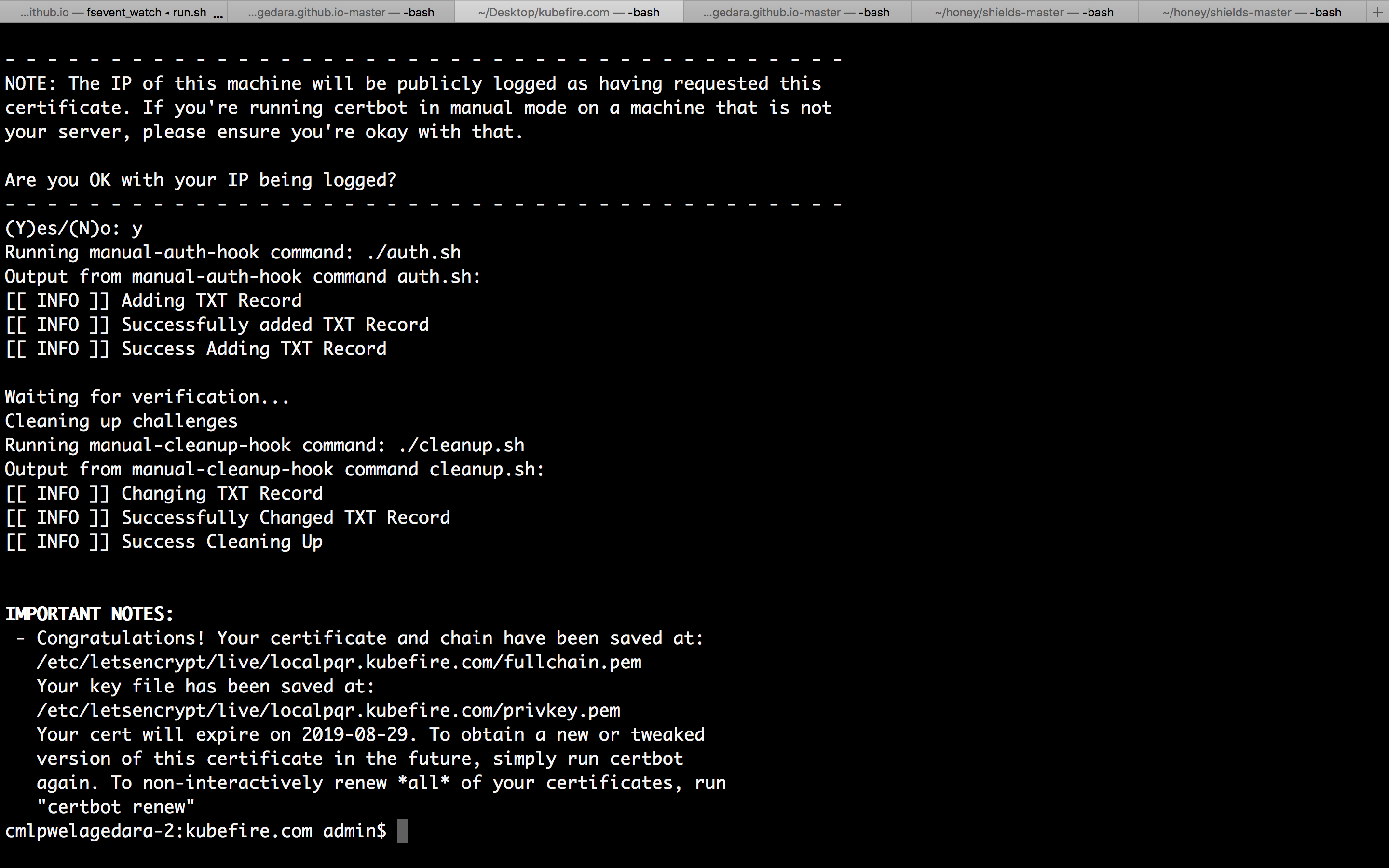
To bypass the Y/N prompt use the below command.
yes | ./run.sh localpqr.kubefire.comHere is the Source Code of the above.
ZeroSSL
ZeroSSL is an online tool that can generate the Certs for you. With ZeroSSL you do not have to install anything on your machine but bare in mind that your Private Keys will be exposed to a 3rd party when you use it.
Here is a link to a ZeroSSL Video Tutorial.