Securing HTTP Traffic to Upstream Servers using NGINX
Nginx / July 05, 2018
How do you secure your backend using HTTPS? I will create a Swagger Node Project to show you how.
swagger project create upstream
cd upstream/
swagger project startSwagger Module for Node will create an endpoint that looks like this( By default the Swagger Document is available on http://localhost:10010/swagger).
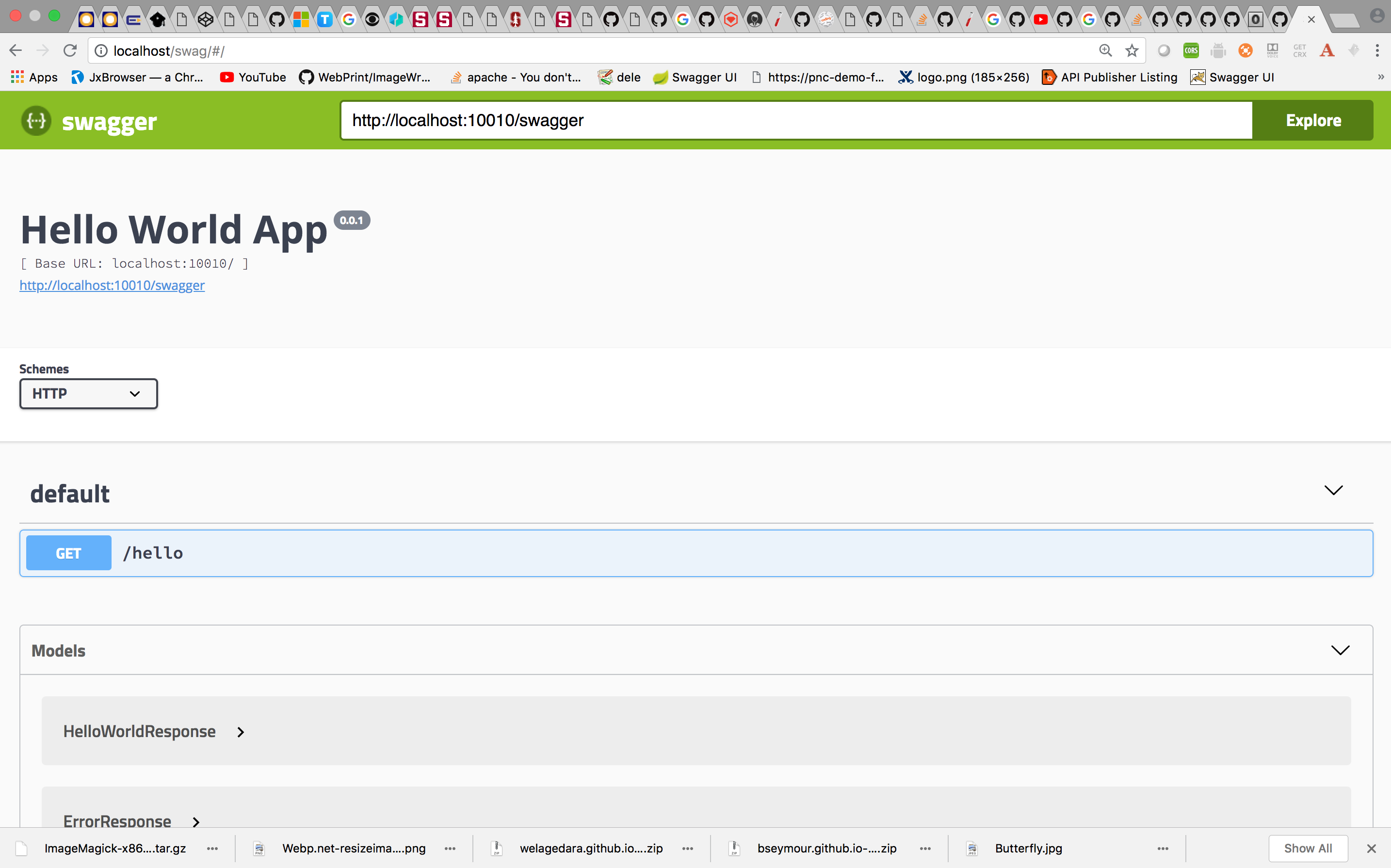
Now let’s configure the NGINX to send the traffic to my upstream server.
Find your NGINX configuration file. On my Mac it was in /usr/local/etc/nginx/ directory.
sudo nano /usr/local/etc/nginx/nginx.confAdd this configuration to that.
server {
listen 443 ssl;
server_name localhost;
ssl_certificate /usr/local/etc/nginx/ssl/tls.crt;
ssl_certificate_key /usr/local/etc/nginx/ssl/tls.key;
location / {
proxy_pass http://127.0.0.1:10010;
}
}Now stop NGINX and then start it.
sudo nginx -s stop
sudo nginxOr simply restart it.
sudo nginx -s reloadYou are all set. Hit the endpoint using the browser( I am using a Self Signed Certificate. Therefore the browser will show an invalid cert message.).
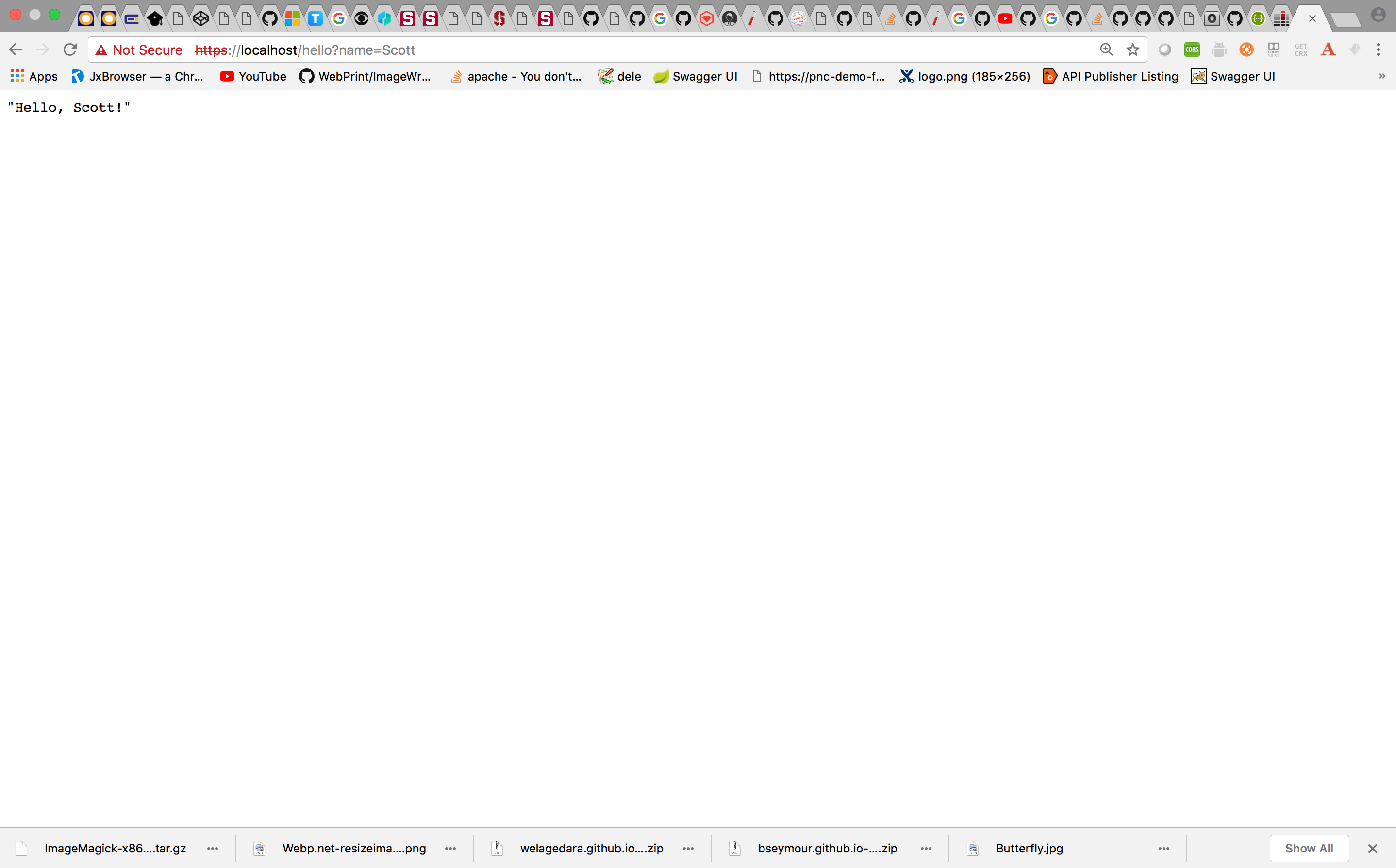
Don’t forget to disable HTTP or to enforce HTTP redirection to HTTPS in your Production Environments.

Icon made by Freepik from www.flaticon.com